Firewall
Firewall Use Cases
Most common to use is Port Forwarding and Inbound Traffic Block.
- Port Forwarding is if you want to open a port from WAN and forward the traffic to a local device
- Inbound Traffic Block block access from a specific address and/or destination
- Forwarding Traffic Block allow/block devices from your local network
- Services Choose which Ports on SPR are accessible
Advanced firewall configuration
- Custom Interface Access - Join a docker bridge or custom interface to SPR networking
- Multicast Proxy -- Configure mDNS, SSDP, and other UDP broadcast services
- Endpoints - Define one-way connectivity rules
Port Forwarding
Set rules to forward incoming traffic (DNAT forwarding).
Add a Port Forward
On the Firewall page expand Port Forwarding and click Add Forward.

In the screenshot all traffic from source address 1.1.1.1 with destination port 8080 is redirected to 192.168.2.106 on port 8080.
Inbound Traffic Block
Block traffic coming into the network at the PREROUTING stage.
Add a Inbound Block
On the Firewall page expand Inbound Traffic Block and click Add IP Block.
 In the screenshot all traffic from source address 1.1.1.1 with destination address 192.168.2.106 will be blocked.
In the screenshot all traffic from source address 1.1.1.1 with destination address 192.168.2.106 will be blocked.
Forwarding Traffic Block
Add rules to block traffic at the FORWARDING stage.
Add a Forwarding Block
On the Firewall page expand Forwarding Traffic Block and click Add Forwarding Block.
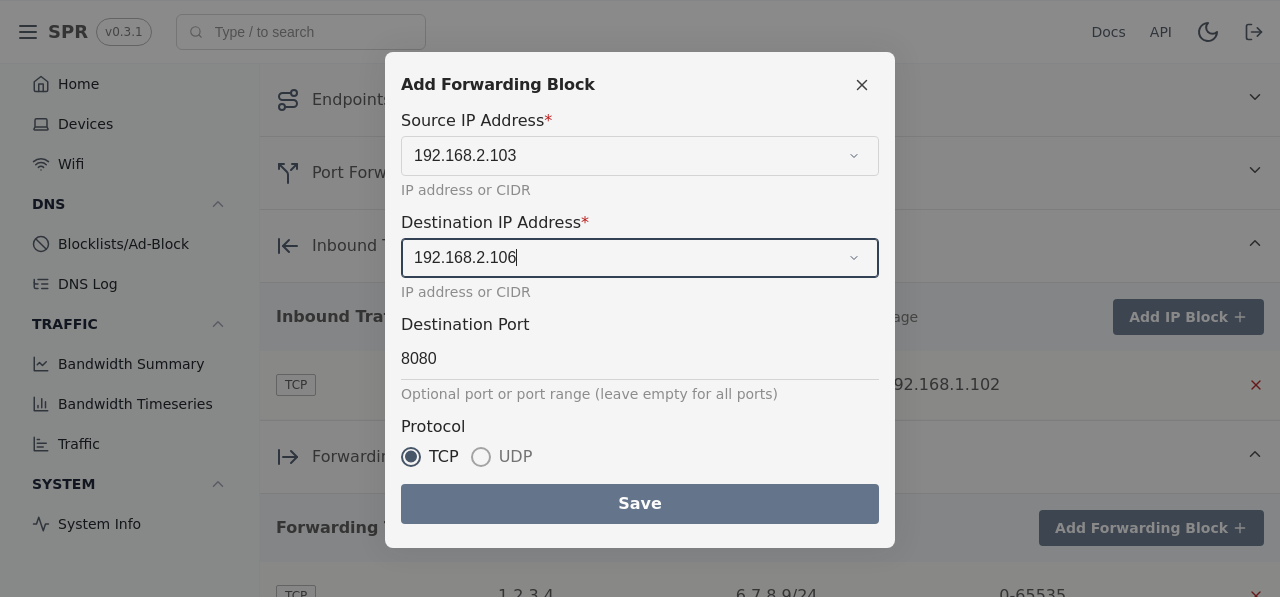 In the screenshot all traffic from source address 192.168.2.103 with destination address 192.168.2.106 on port 8080 will be blocked.
In the screenshot all traffic from source address 192.168.2.103 with destination address 192.168.2.106 on port 8080 will be blocked.
An example use case would adding the LAN policy to a device but wanting to block access on some outgoing ports or IPs.
Custom Interface Access
Manage network access for custom interface names and control access for docker networks.

Use this to forward traffic to an interface running in a separate container.
See more in the repository for the spr-mitmproxy plugin for how this feature can be used.
Multicast Proxy
Set multicast ip:port addresses to proxy between devices. This allows discovery services such as SSDP/Zeroconf and mDNS in SPR. By default only SSDP and mDNS are on. You may need to enable PTP or other services for streaming and device sync. If something is not working as expected, let us know, by filing an issue
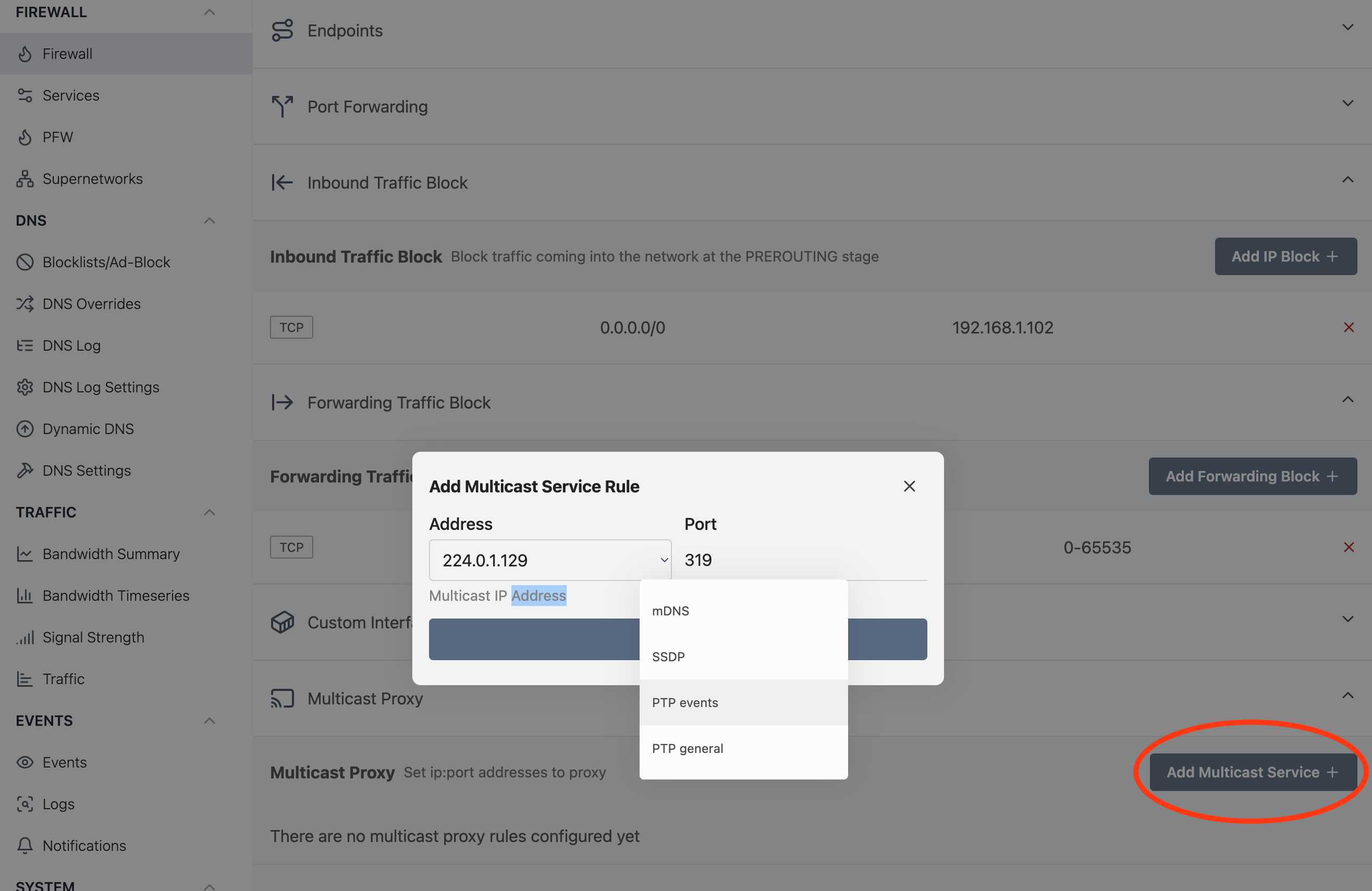
Optionally, a tag can be applied to a service to apply proxying to only a subset of devices that have the same tag.
Endpoints
Service Endpoints serves as helpers for creating other firewall rules, as well as one-way connectivity from devices to the endpoint when they share a tag.
When devices are in the same group they have full access to each other. Device with the LAN policy have one-way access to all devices via NAT.
Endpoints create a quick way to apply one-way connectivity a specific destination, by applying tags.
- Create an Endpoint definition

-
Apply a tag
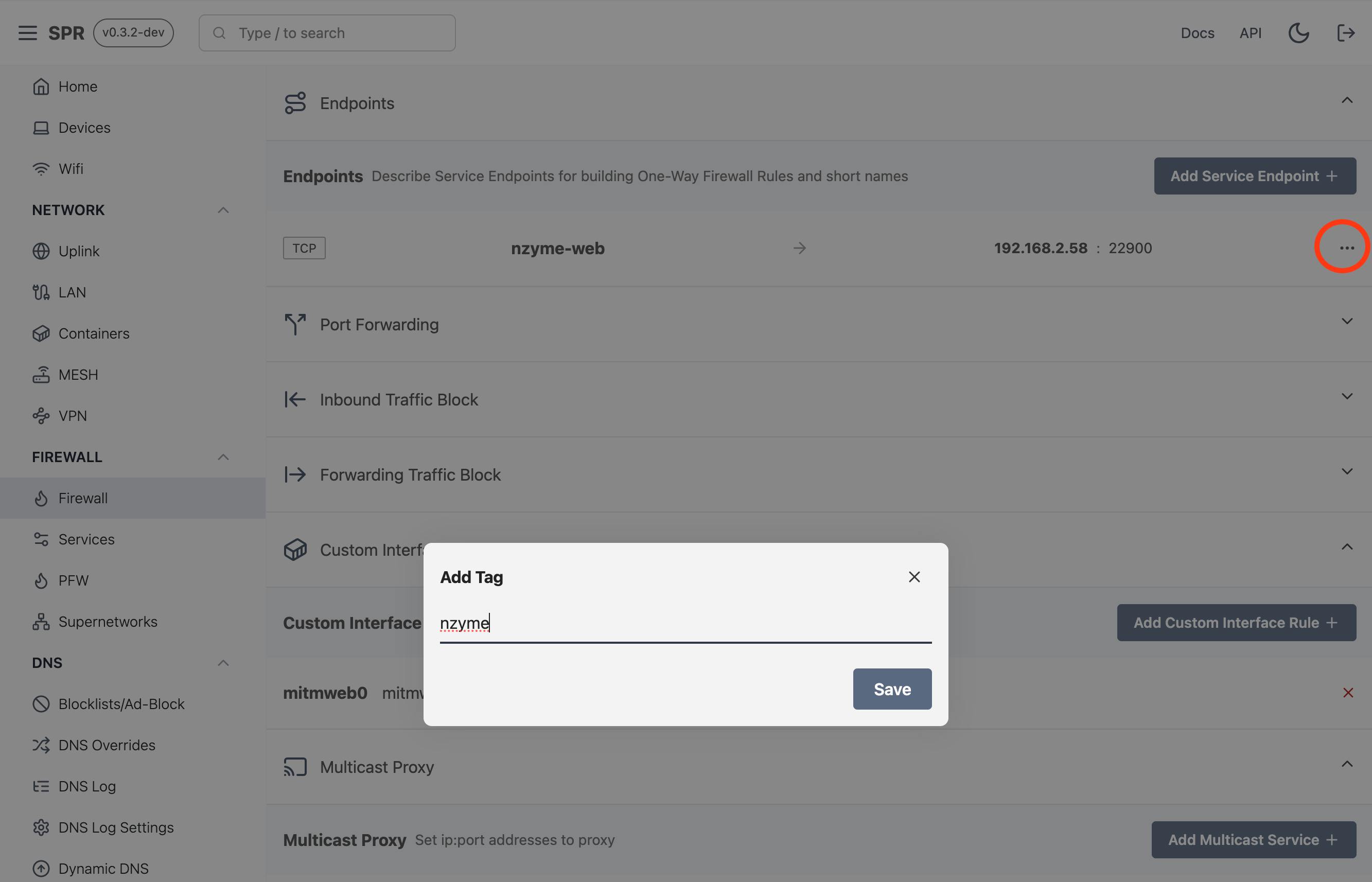
-
Apply the same tag to the device that should have access to the endpoint
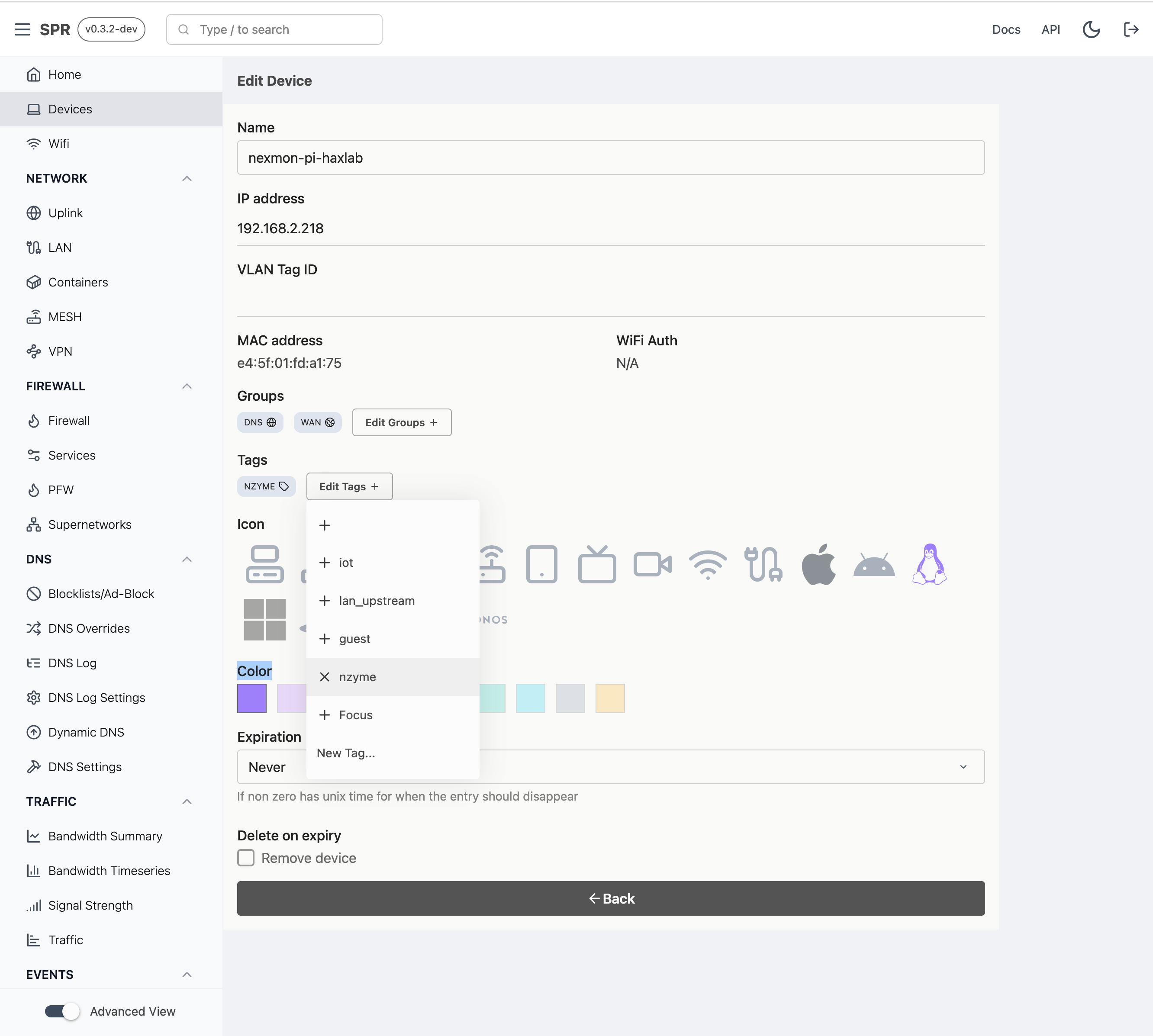
-
Example of device access before and after it has the tag
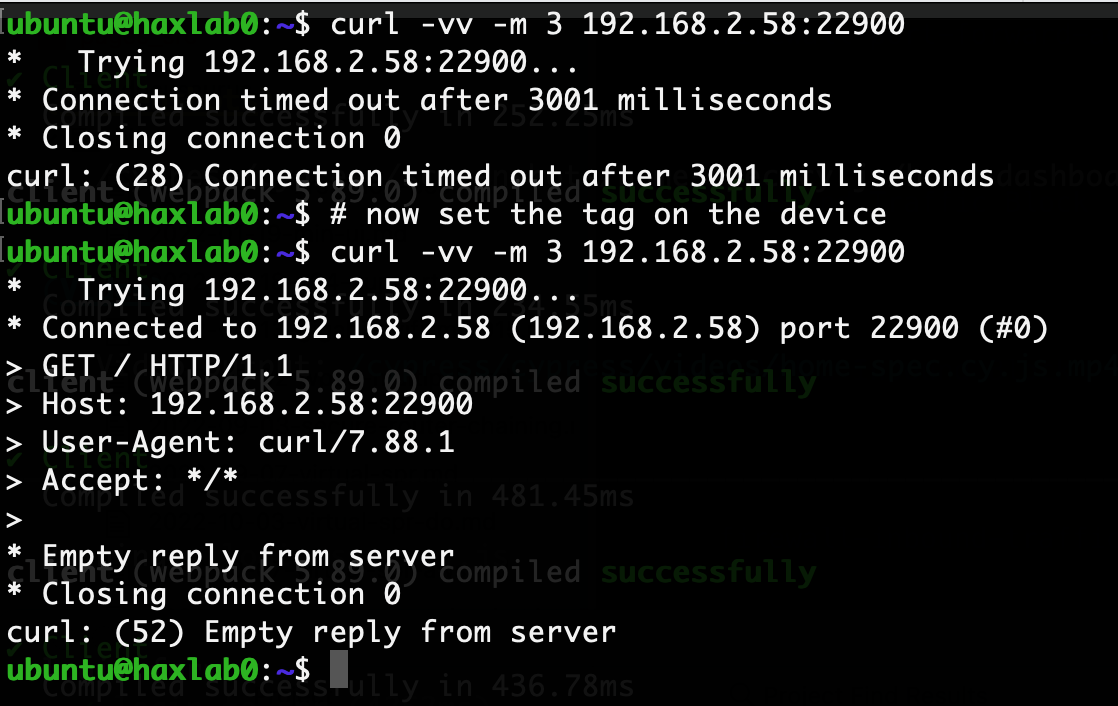
The other side, 192.168.2.58, does not gain access to the device on 192.168.2.218 beyond receiving TCP connections on :22900.
Services
The services view controls firewall settings for the SPR router itself. The Ping settings control if SPR can be pinged. These are on during setup but disabled by default after.
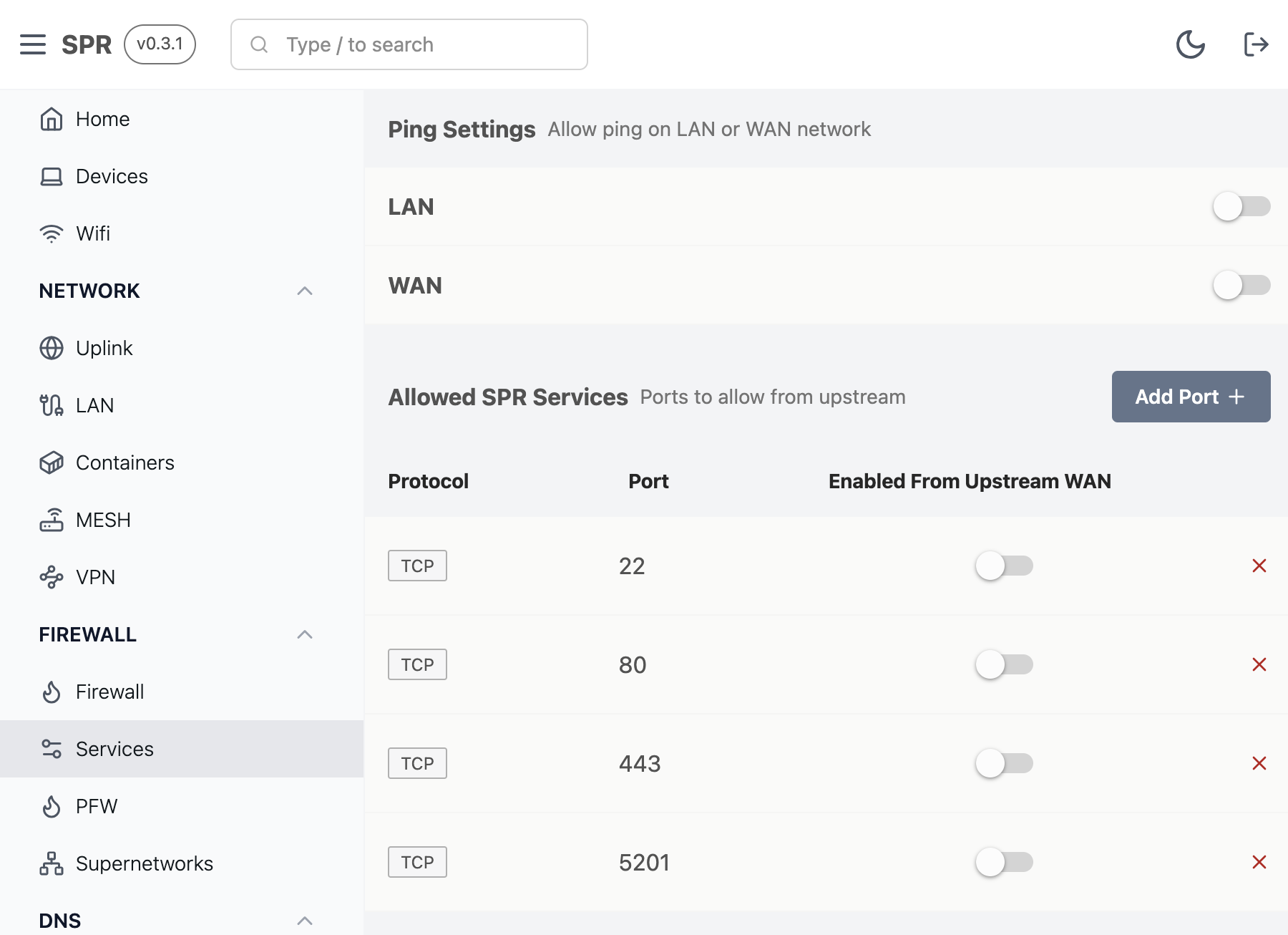
Working with Service Ports
The allowed SPR services are default on for all devices. In a future release tag support will be improved to further restrict port access to the API (tcp 80) and SSH (tcp 22) on SPR.
To remove access for LAN devices, delete the service entry.
To allow access to the service from the Uplink interface, turn the slider to on ("Upstream WAN").
Multicast Settings
SPR uses a multicast UDP Proxy to relay multicast traffic between devices.
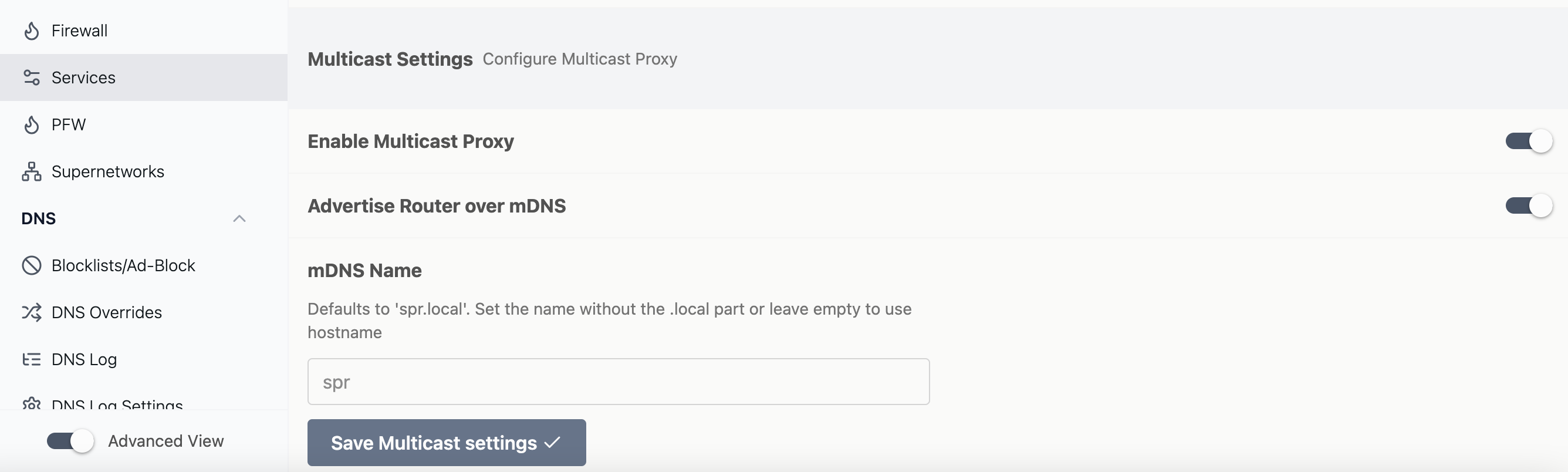 Set the "Enable Multicast Proxy" to false to disable the proxy and all mDNS settings.
Set the "Enable Multicast Proxy" to false to disable the proxy and all mDNS settings.
The "Advertise Router over mDNS" toggles whether or not the proxy will respond to mDNS name requests on the uplink interfaces.
This makes it possible to discover SPR with querying 'spr.local' on systems that are aware of mDNS.
The mDNS name can also be customized.