Policies, groups and tags
To isolate networks and devices SPR is using policies, groups and tags:
- Policy for network access, internet
- Group Fine grained access within networks, isolation
- Tag Control traffic, ad block
Policies
- wan internet access
- dns for domain lookups, block/filter dns
- lan access to all other local devices
- lan_upstream allows the device to query LAN addresses from rfc1918 upstream of SPR
wan and dns is enabled by default. Add the device to lan sparingly, as this grants it access to all other devices. You can create groups and rules later for defining more specific access.
WAN policy
Example WAN policy, devices with the policy can access internet:
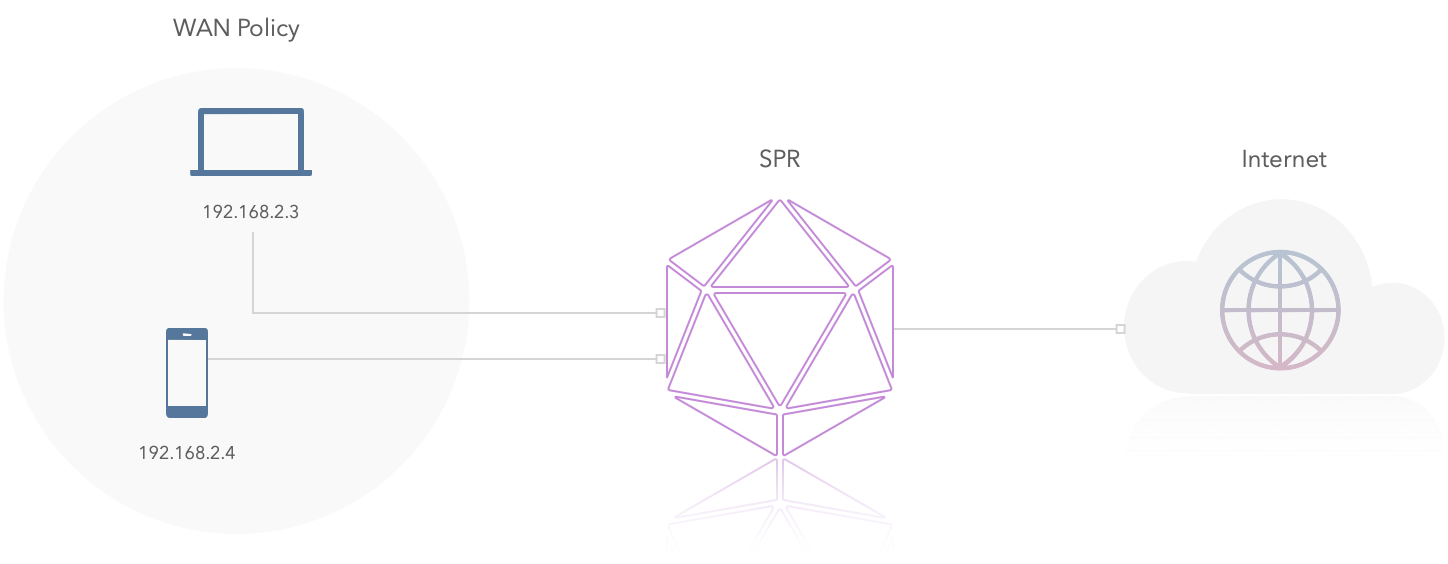
dns policy is needed for dns lookups on wan network
LAN policy
Example LAN policy, the two devices can talk to each other:
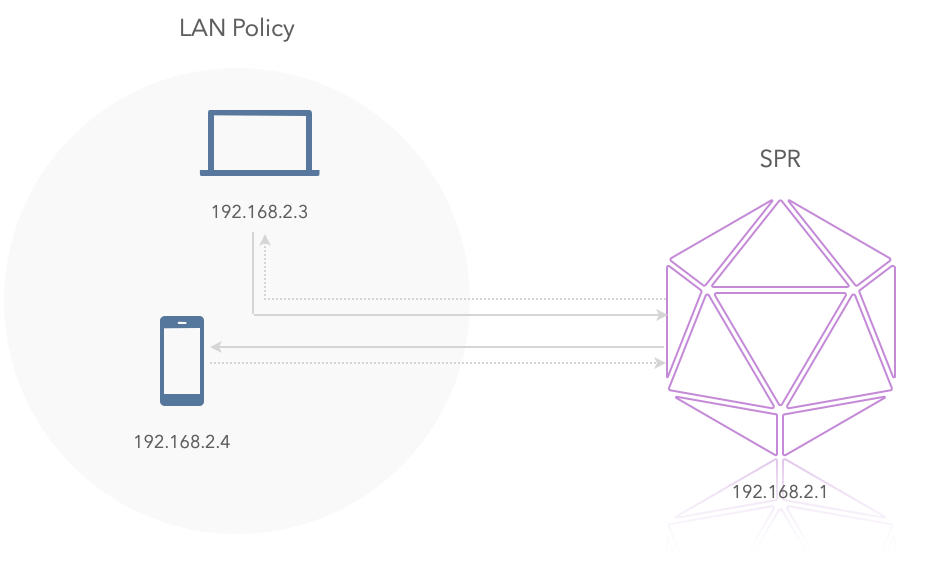
Groups
Devices assigned to a Group can intercommunicate (TCP, UDP & ICMP). A firewall rule can be used if only a particular port should be reachable.
If a device does not have the lan policy and is not in a group it's completely isolated.
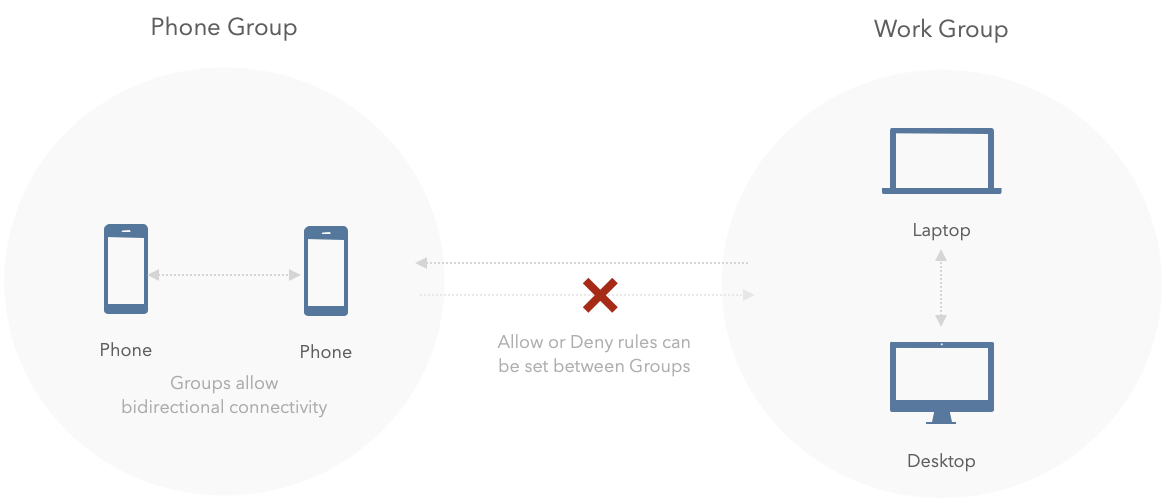
Use cases and examples
In this example the work group can access devices within the phone group (using the lan policy), the work group is not visible for the phones:
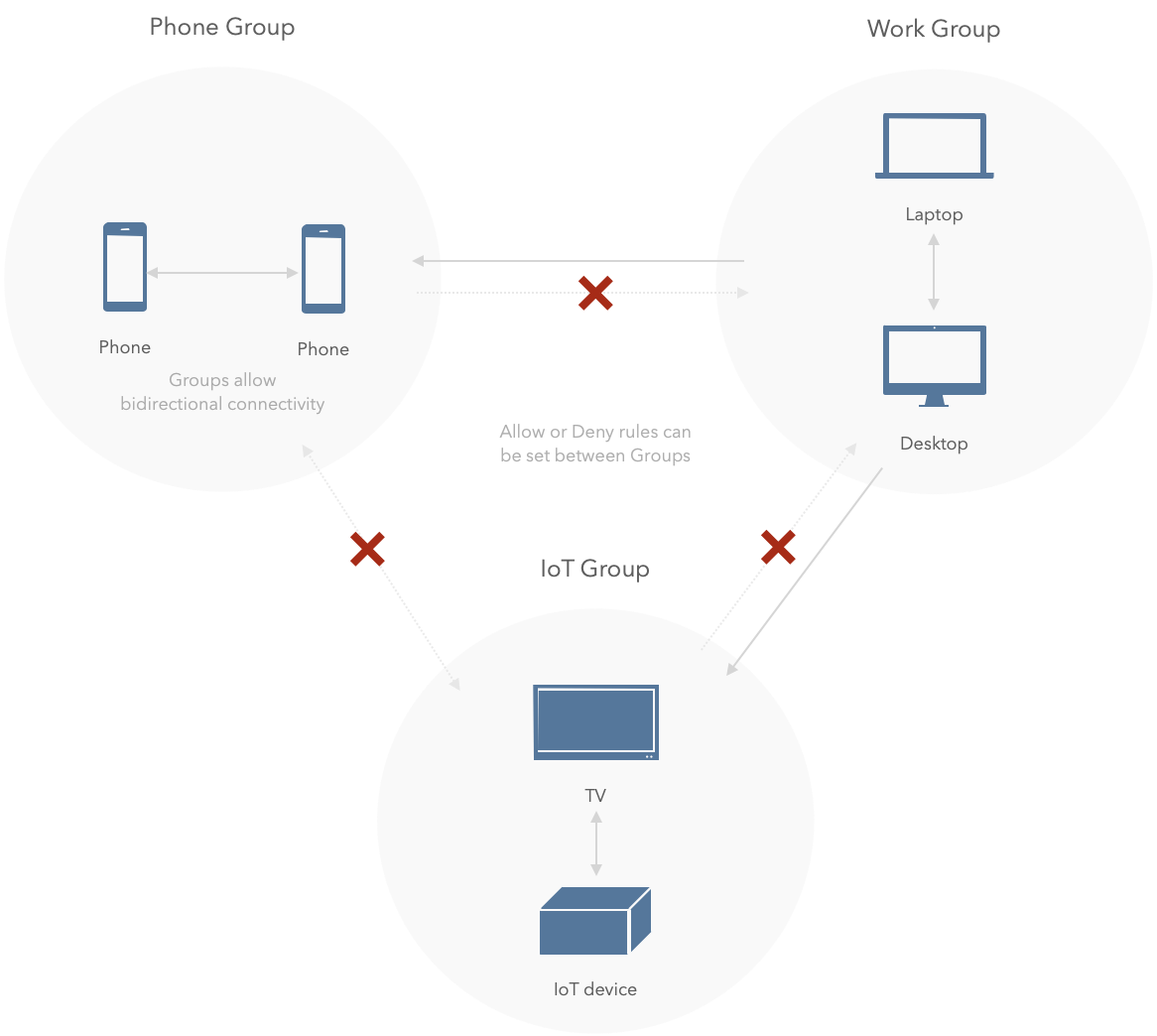
Isolated IoT Devices
Here Work group have the lan policy and can access all the groups, the phones and iot devices can't see each other or access the work environment:
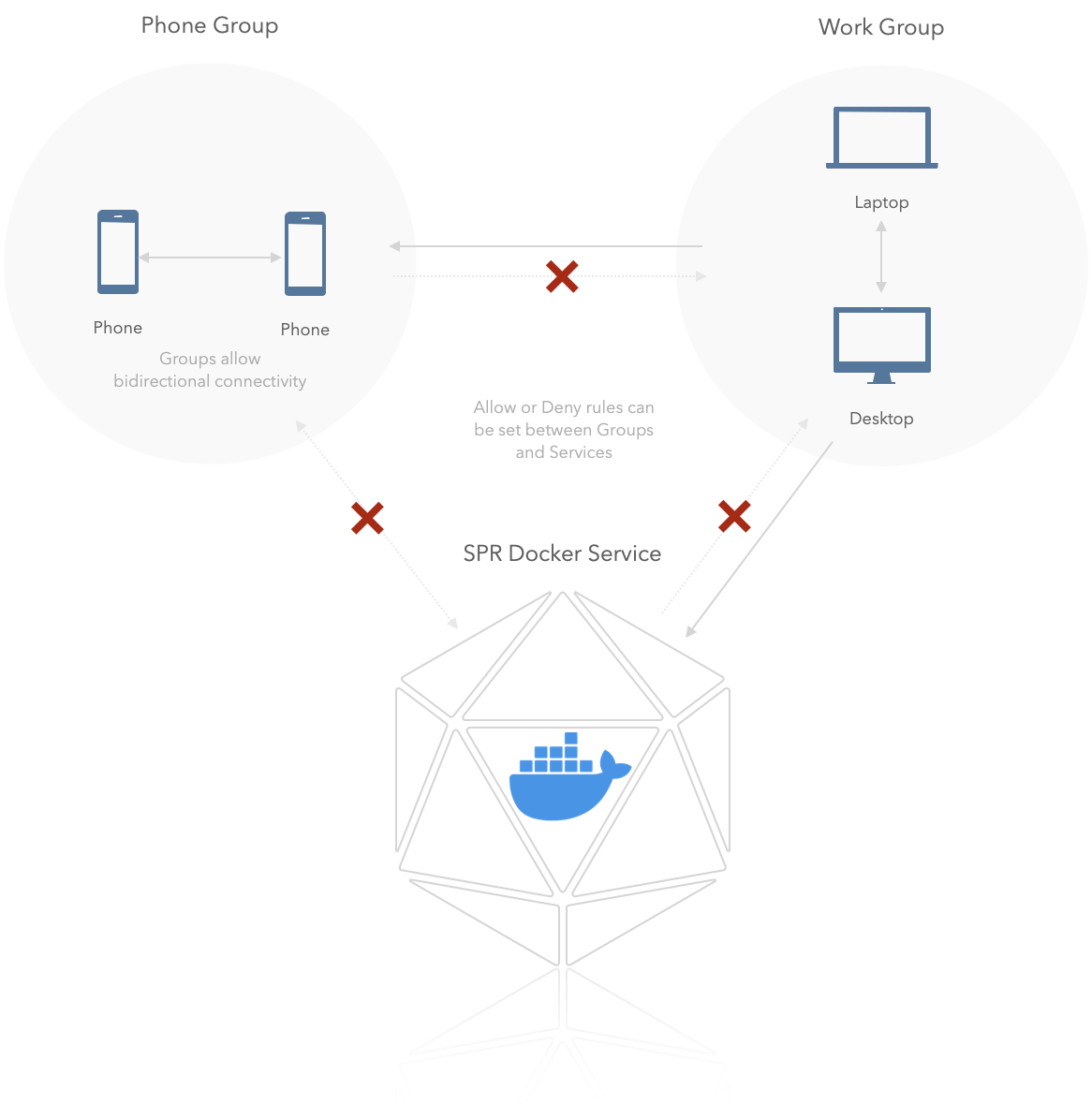
Docker Service
Devices in the work group can access the docker service, but the service can't access any of the groups.
Tags
Tags can be used to apply blocklists for specific devices: Block Lists Tags