Advancing DecoyAuth is Key to Making WiFi & WPA3 More Secure
Pioneering WiFi Security
Supernetwork's flagship project, SPR, is a pioneer in WiFi security and we've supported multi-pass WPA3 from the inception of the project in 2022.
To use newer protocols like WiFi 6-e and 7, users can not fall back to WPA2, which is excellent since WPA2 suffers from passive sniffing & password cracking attacks.
WPA3 provides a zero knowledge proof: there's no handshake to sniff and crack -- but the protocol is rigid and makes it hard to support multi-pass. So most products only do it for WPA2 sadly, meaning they can't operate on 6-e or 7. This leaves users making more bad security tradeoffs. SPR works to give people the best security choices by default but the user experience could still vastly improve.
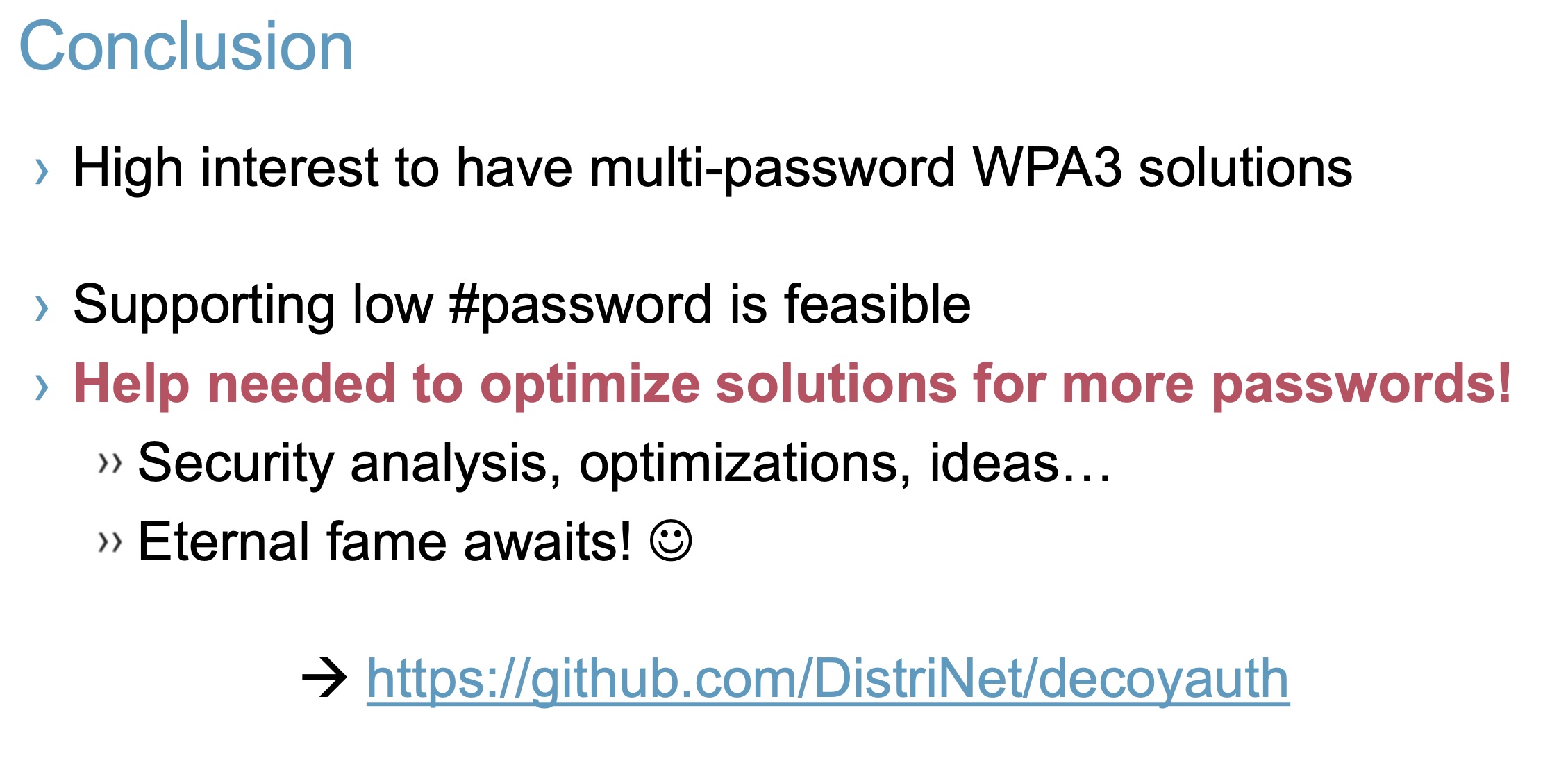
A new project, DecoyAuth, by Mathy Vanhoef, seeks to do that just that and make WPA3 better support multipass.
The project was presented at PAKE25 and the slides are here.
The Challenges of WPA3 Multipass
One of the key aspects of multipass is that the password's also the secret that marks the identity of the device. With WPA2, an AP enumerates the passwords it has to identify which devices authenticated, and map it to its VLAN/network.
With WPA3, the zero knowledge proof commitments in SAE mean the AP can only attempt one password per authentication. This leaves the MAC as the guide for identifying a device. And the protocol in effect can only accept new devices with a wildcard key.
This is what SPR does to support multi-auth for WPA3. But it has several shortcomings:
1. Only one device can be added at a time
There's no way to add N devices with N unique passwords out of order. It must be done sequentially,
during a "registration" phase. This is the Add Device flow on SPR. When the new device shows up, the MAC is assigned to that password.
2. MAC Randomization
If a device randomizes it's MAC, it must be reassigned to the network, or a fixed MAC should be set. This means there's now a privacy tradeoff where the MAC can't rotate
3. Password Sync Breakage
When Apple devices force password syncing, they all have different MACs. SPR admins have to share the wifi password between all the apple devices, limiting isolation between the ecosystem. For example, an apple tv, apple watch, and iphone all end up being able to impersonate each other.
Addressing these would be amazing for SPR users since they can enjoy multipass without worrying about the above which are more or less a "security tax". We should stop designing protocols with security taxes, the best security should be free and effortless, by default.
Existing Workarounds
The IEEE standard does provide a way to pass an identity for SAE to help work around this. QR Codes can specify an identifier. However many clients dont allow manual entry of the identifier when entering a password. This limits how well this can be applied.
Another shortcoming Vanhoef points out in DecoyAuth is that the identifiers leak in plaintext, and allow user tracking.
DecoyAuth Proposes Advancing Oblivious PAKE (O-PAKE) to resolve WPA3 Multipass
The naive base case is to perform the SAE protocol, for each password, in parallel. This means as more devices are on the network, this is not really feasible, as this causes a linearly increasing amount of packet spam.
O-PAKE protocols seek to instead allow peers to efficiently try multiple passwords using interpolation.
The DecoyAuth Project explores solving applying O-PAKE for WPA3's Dragonfly.
The current best proposed approach has the following characteristics where N is the number of passwords:
- A polynomial interpolation can be broadcast to all clients (with O(n) size)
- AP does O(N) work to authenticate and identify a client
A Call To Action
The need for user friendly WPA3 Multipass is clear.
- The current OPAKE solution breaks down as clients are added. Can many clients be supported?
- The protocol needs cryptographic security analysis