Authentication, Association, and Authorization in 802.11 WiFi
Association in the 802.11/ WiFi World comes in the "loose" variety of the term, and why Hostapd disconnect events are confusing...
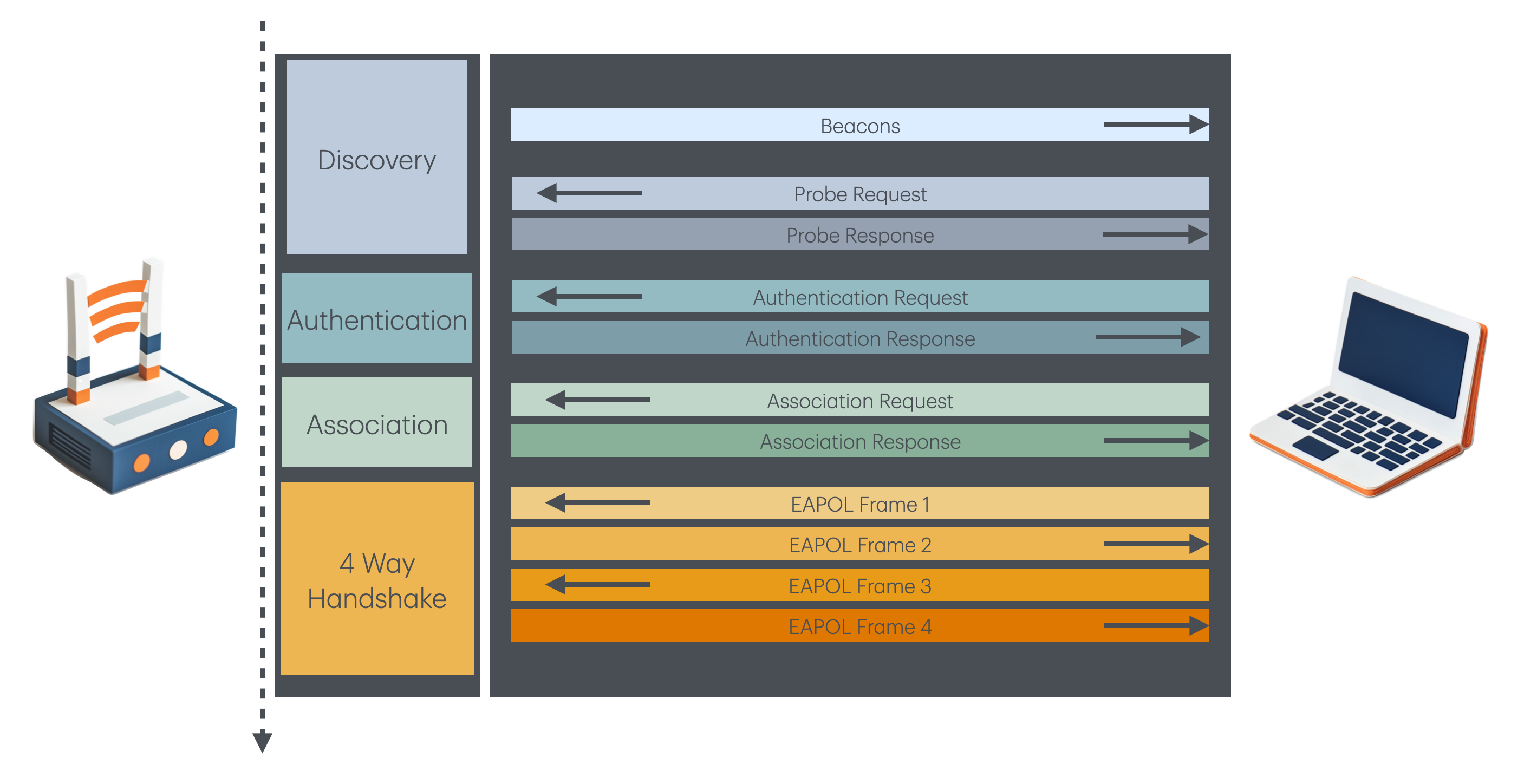
As a quick recap: when a station connects to an Access Point, it goes through a series of request/reply interactions. Several frames are in play including Probes, Authentication, Association, and finally Data frames with EAPOL. The EAPOL payloads perform all the fun cryptography with the passphrase for WPA2, WPA3, and 802.1X Authentication mechanisms.
Association is Not Authentication
As shown in the diagram, the flow has Authentication, Association, and then EAPOL. The Association frames happen before the cryptography is happening with WPA2. Nothing is authenticated at this point. Association lets an Access Point be aware that a Station has associated itself and will begin sending data for the AP to receive.
Authentication is Not Authentication
Wait a second. Authentication already happened? Why is EAPOL happening?
Well it turns out that the Authentication frames for secure wifi today never do authentication, because they only support insecure cryptography like RC4/WEP under "Shared Key Auth". Because the frame format was hard to extend and keep backwards compatible, 802.11 went down the path of going with "Open System Auth" and handling authentication later. So today we let WEP rest in the crypt :-)
Authorization Happens With EAPOL
So once the EAPOL 4-way handshake is happy, we have authentication, and the Access Point authorizes the station to send data. All is well. Hostapd will set the [Authorized] flag on the station as well to reflect this.
The takeaway here is that when you're building a WiFi system, "associated" stations have not done much more than express an interest in connecting and authenticating. This is convenient for example for knowing if there's a station out there that's confused.
When SPR runs as a router, it can alert on WiFi Auth failures -- and it will also warn in the Devices view about stations hanging out that haven't authenticated with EAPOL. This helps users debug their wireless environment when something can't connect.
What Is A Disconnection in the Ether Anyway?
So we've covered the connection half of these nebulous things in 802.11 named Authentication & Association.
But how does disconnection work? Well devices/APs can send a Deauth / Disassociate frame to let the AP know it's leaving. For more details on these check out Deauthentication Frames Explained.
But we have no physical wire. A station is not obligated to send these along, and very often they don't, it would be extra packets on the medium to be aggressive about sending these when leaving the environment. The protocol designers are very aware that 802.11 transmission is half-duplex. Only one system can transmit over a channel at a time, and senders have to wait for a transmitter to complete their frame, so skipping these is not a bad thing
Which leads to the next confusing thing:
HostAP Uses Radio Presence for Inactivity
Activity in the hostapd world means that when a station's MAC address is seen transmitting, it's considered active.
This means that a client could remain associated with an AP, even if it's connected to a new AP. The disconnect event could then happen long after the station has moved on.
To make this a little smoother, hostapd also provides an option to disconnect sooner.
#
# The inactivity polling can be disabled to disconnect stations based on
# inactivity timeout so that idle stations are more likely to be disconnected
# even if they are still in range of the AP. This can be done by setting
# skip_inactivity_poll to 1 (default 0).
#skip_inactivity_poll=0
In our Mesh support -- we can't rely on HostAP disconnect events to rewire devices between mesh nodes. Instead we use the authorization to the new Mesh AP to refresh the routing.
Conclusion
This post adds clarity to the confusion in the 802.11 world's usage of the terms Authentication, Association, and Authorization. They are not as straightforward as they sound because of the winding history of WiFi Authentication.
Looking to dive into the 802.11 Protocol?
Check out our Reference WPA2 Access Point in Scapy. It's been featured in Defcon Qualifers and Finals, our Turtles challenges, as well as the Midnight Sun CTF. It handles everything needed to let modern devices connect with WPA2 Authentication and send traffic.